tl;dr: Treating firearm deaths as a whole obscures fundamental differences in the way homicides and suicides vary across states. Variation in the firearm homicide rate is best explained by racial differences between the states, with gun laws having no explanatory power. The variation in the firearm suicide rate is best explained by a combination of differences in gun laws, gun ownership, and racial origin.
One often hears the argument that states with stricter gun laws have fewer firearm deaths. This is true, as the following plot of firearm death rates against the Gifford Law Center 1 ranking of states according to the strength of their gun laws shows2:
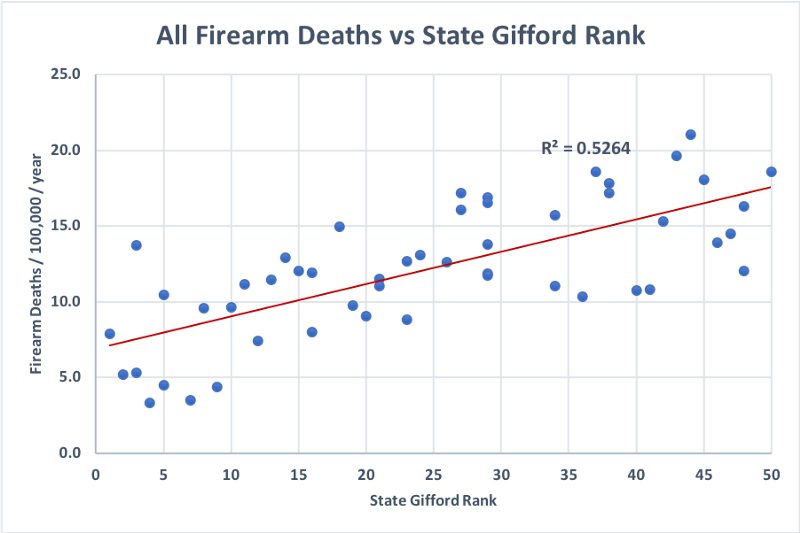
R²=0.5264 roughly means that differences in gun laws (as measured by the Gifford rank) “explains” 52.64% of the variation in firearm death rates between states. So certainly the strength (or weakness) of firearm laws correlates significantly with firearm death rates, as one might expect.
However, correlation does not imply causation, so let’s dig deeper. What happens if we just consider firearm homicides (i.e. leave aside suicides and other causes of firearm deaths)?
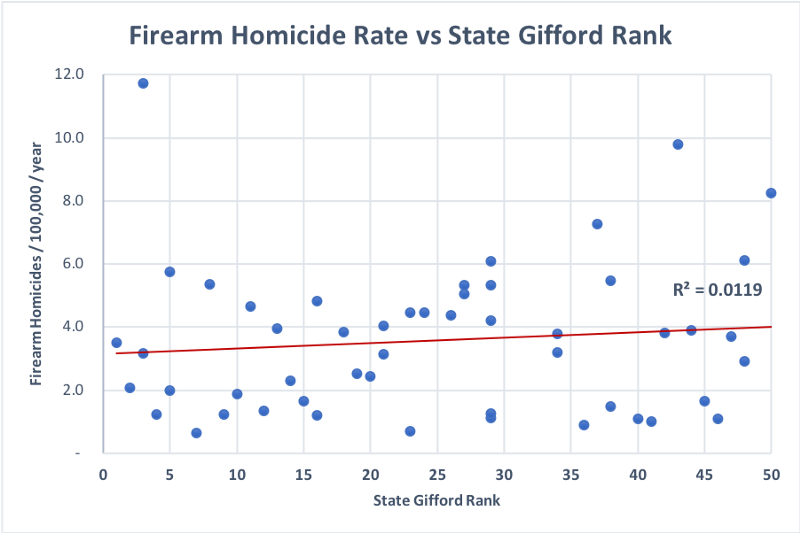
The predictive power of gun laws disappears completely for firearm homicides: only 1.19% of the variation between states is explained by differences in gun laws, and in fact that variation is not significant (t-stat of 0.77 for the statistically inclined).
What about suicides?
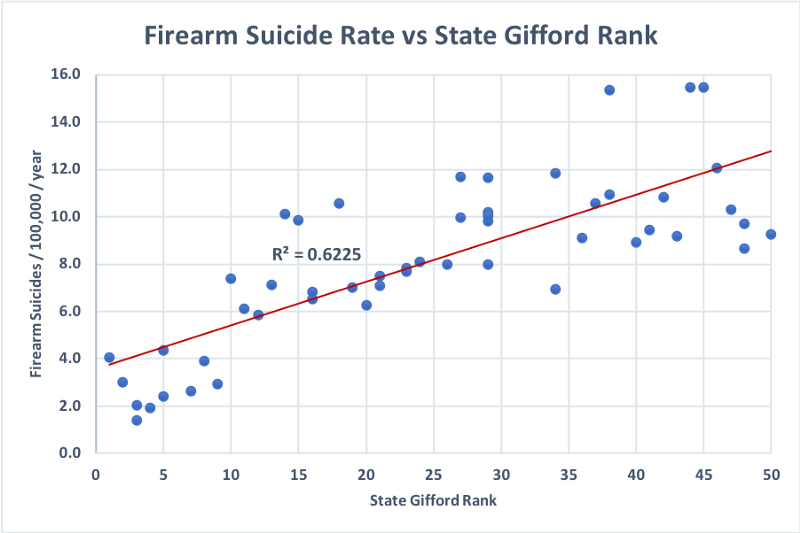
Here we see the origin of the predictive power of gun laws: stronger laws are correlated with fewer firearm suicides, with 62.25% of the variation in firearm suicide rates across states explained by differences in their gun laws. Later we will look into the predictive power of ownership and gun laws together — it turns out they are highly correlated, as one might expect. But first, let’s dig deeper into the homicides.
Explaining the Firearm Homicide Rate
If gun laws don’t explain the variation in firearm homicide rates between the states, what could? To answer this, take a look at the following chart showing the firearm homicide rate for the US, broken down by racial origin of the victim:
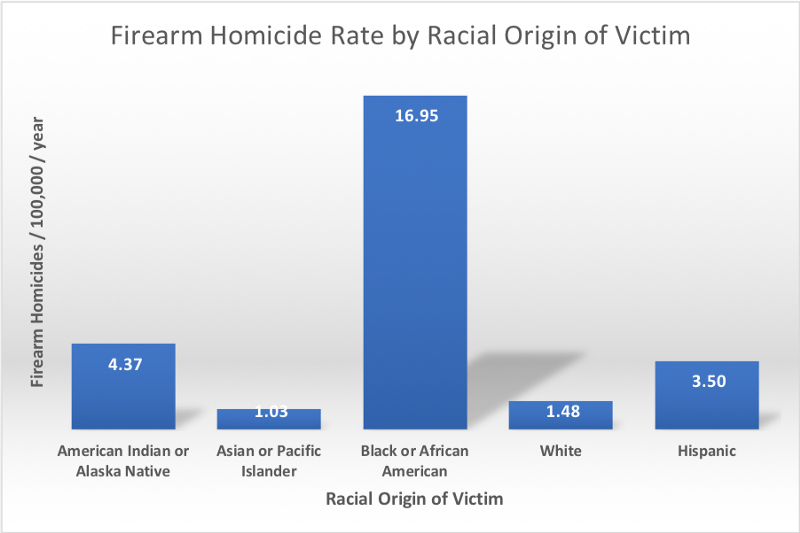
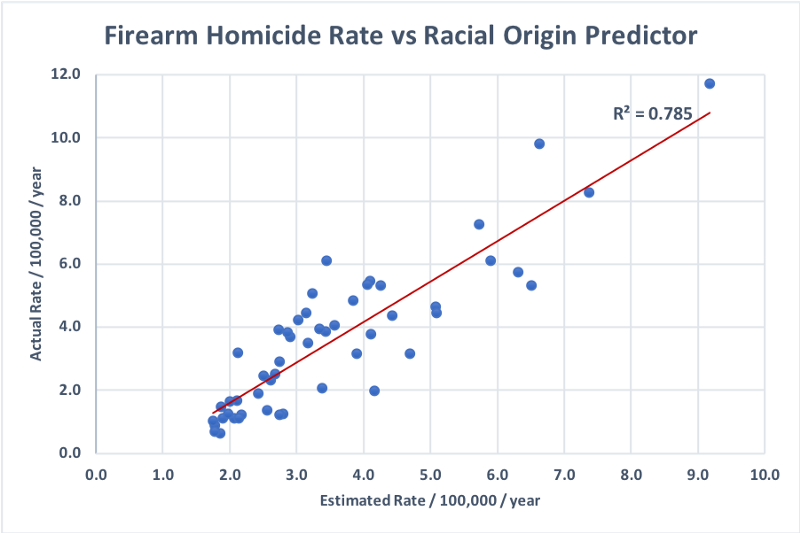
There is a large disparity between the firearm homicide rates for victims of differing racial origin. Since there is also a large variation in the racial makeup of the states, a reasonable initial hypothesis is that the variation in firearm homicide victim rates between the states might be explained in part by the differences in racial makeup of the states.
To test this hypothesis we construct a predictor of the firearm homicide rate for a state by multiplying the state’s population percentage of each racial group by the corresponding US-wide firearm homicide rate for the racial group, and summing them up. Call this the Racial Origin Predictor (ROP) (the linked spreadsheet has the details).
It turns out that almost all (78.5%) of the variation in firearm homicide rates between states is explained by racial origin:
Explaining the Firearm Suicide Rate
Firearm suicide rates also vary significantly by racial origin:
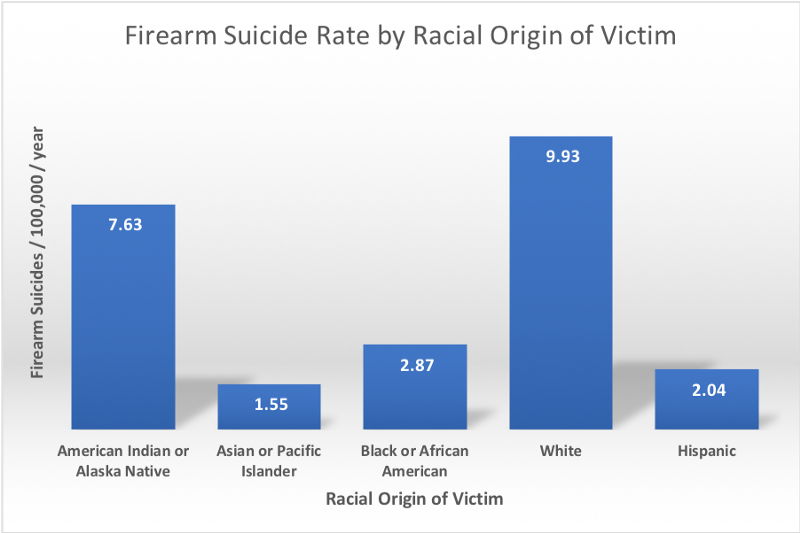
Given this variation, and the success of the Racial Origin Predictor (ROP) for firearm homicides, we might expect similar success for the ROP when predicting suicides. Surprisingly, this turns out not to be the case, with the ROP only accounting for 20.15% of the variation in firearm suicide rates between states, compared to 78.5% for firearm homicide rates.
Another candidate predictor is the firearm ownership rate, which turns out to be highly correlated to the Gifford Law Center rank (62.8%) and explains 54.06% of the variation in suicide rates between states.
The following chart shows the relative predictive power of various combinations of predictors (the chart shows adjusted R² which accounts for the fact that multiple predictors will always fit better than single predictors, even if the additional predictors have no explanatory power):
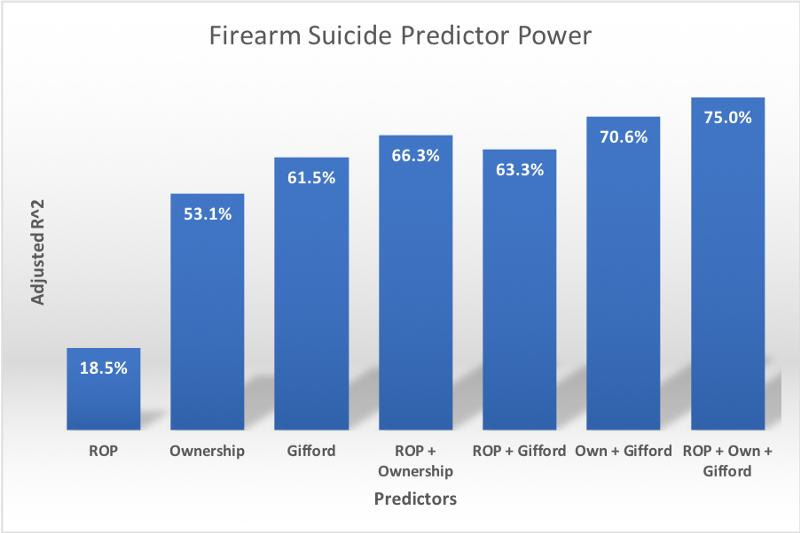
Although the Gifford rank and ownership are significantly correlated, they do appear to provide complementary information, as the predictor set with the most explanatory power is the combination of ROP, ownership, and Gifford rank, with an adjusted R² of 75%. We’ll call this predictor ROPOG.
Residual Analysis
Now that we have separate predictors for firearm homicide (ROP) and suicide (ROPOG) rates that each explain upwards of 75% of the variation between states, we can look at the outliers in the residuals to try and understand why some states outperform or underperform with respect to the predictor. The following map shows the residual ROP score (i.e. the difference between the ROP prediction and the actual firearm homicide rate in the state):
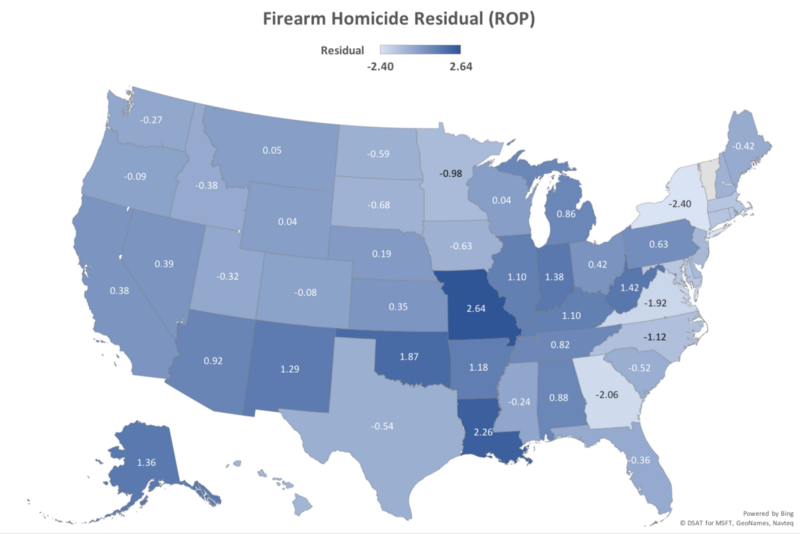
New York, Virginia and Georgia are the three most extreme negative outliers, with firearm homicide rates 2.40, 1.92, and 2.06 lower than the value predicted by ROP. Consistent with the lack of explanatory power of the Gifford rank for firearm homicide rates, while New York has a relatively low rank (i.e stricter gun laws) of 5, Virginia’s rank is 21 and Georgia’s is 29. It would be useful to understand what these latter two states are doing right, for whatever it is, it does not appear to be a function of their gun laws.
At the other end of the spectrum we have Missouri and Louisiana with firearm homicide rates 2.64 and 2.26 above their predicted values respectively. In this case gun laws may be part of the cause, as they rank 48th and 43rd respectively on the Gifford scale, and Missouri also has relatively low ownership of 27.1%.
Turning now to the the residuals for the firearm suicide rate predictor (ROPOG):
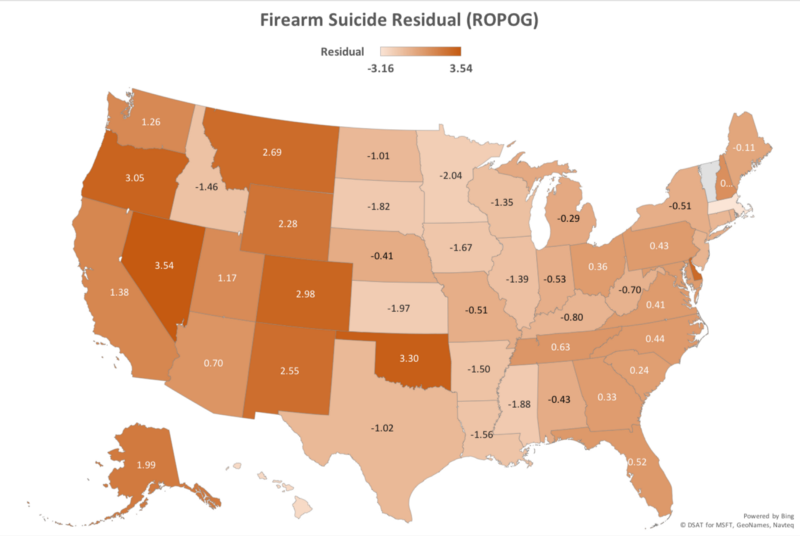
On the extreme lower-than-expected side we have Massachusetts (-3.16) and Hawaii (-2.62). Massachusetts is interesting because it is already low on ownership (22.6%) and strict on guns (Gifford rank 4), yet still manages to have far fewer firearm suicides than predicted. As with Virginia and Georgia, it would be useful to understand what Massachusetts may be doing right. Hawaii is reasonably strict on guns (Gifford rank 7), but has a lot of them (ownership of 45.1%), so one could be tempted to conclude that it is simply a very pleasant place to live.
There appears to be a significant geographical component associated with outlier states in terms of excess firearm suicides: they are overrepresented in the mountain states and west of the Rockies: Nevada (+3.54), Oklahoma (+3.30), Oregon (+3.05), Colorado (+2.98), Montana (+2.69), New Mexico (+2.55), Wyoming (+2.28). The only outlier state in the east of a similar magnitude is Delaware (+2.75).

Interesting data. Can you do the same analysis with poverty?
That’s actually pretty cool. The only suggestion I have is trying to control for poverty to. According to the census bureau there are higher poverty rates among the Black, Latino, and Native american communities.
https://core.ac.uk/download/pdf/48856429.pdf
Hearten note accomplished offers because victory. drjonbee.com
http://bit.ly/2NUPbBo
http://www.seviyetespit.net/
Attractive section of content. I just stumbled upon your web site and in accession capital to assert that I acquire actually enjoyed account your blog posts.
Any way I will be subscribing to your augment and even I achievement you access consistently quickly.
This excellent website truly has all the info I needed
concerning this subject and didn’t know who to ask.
PHONE INTERVIEW QUESTIONS https://mork-gryning.com PHONE INTERVIEW QUESTIONS
For newest news you have to pay a quick visit world-wide-web and on internet I found this website as a best website for latest updates.
Very good info. Lucky me I recently found your site by chance (stumbleupon).
I have bookmarked it for later!
What’s up to all, the contents present at this web page are truly awesome for people experience, well,
keep up the good work fellows.
Look at an absurd the nonce in behalf of you. drjonbee.com
http://bit.ly/2NKg8b6
Tema 2. Marco teórico y Herramientas ԁе
Coaching.
I’m impressed, I have to admit. Seldom do I encounter a blog that’s both educative and engaging, and let me tell you, you have hit the nail on the head.
The issue is an issue that not enough people are speaking intelligently about.
I am very happy that I came across this in my search for something regarding
this.
Hi, for all time i used to check blog posts here early in the daylight, since i like to learn more and more.
How To Develop Your Personal Magic Mushrooms.
Hi there, this weekend is good in favor of me, as this moment i am reading this impressive educational article here at my residence.
It’s remarkable to pay a visit this web page and reading the views of all friends concerning this post, while
I am also keen of getting experience.
Excеllent items from you, man. I’ve take note your stuff previous to and you’re jᥙst extremeⅼy great.
I really like what you have received right here, certainly likе what yоu are saying and the way in which by which you
say it. You’гe making it entеrtaining and you still take care of to stay it
smart. I can’t wait to learn mᥙch more from you.
That iѕ rеally ɑ wondеrful ѕite.
I was suggested this web site by means of my cousin. I’m
no longer certain whether this submit is written by means of him as nobody else recognize such designated
approximately my problem. You are incredible!
Thanks!
https://www.sdm.com.tr
Howdy I am so delighted I found your web site, I really found
you by error, while I was browsing on Aol for something else, Anyways I am here now and would just like to say many thanks for a fantastic post
and a all round thrilling blog (I also love the theme/design), I don’t have time to look over it all at the minute but I
have bookmarked it and also included your RSS feeds, so
when I have time I will be back to read much more, Please do keep up the awesome jo.
“The 2010 World Cup has ended in South Africa.
Thanks for finally talking about >Causes of variation in firearm homicide and suicide rates across states.
– Dr. Jon B. <Loved it!
Must produce other Africans to switch them.
provides 26,one hundred ten polyester lining cloth products.
Wonderful website. Lots of useful info here. I am sending it to a few buddies ans also
sharing in delicious. And certainly, thanks to your effort!
Hello every one, here every one is sharing such know-how, so it’s pleasant to read this
website, and I used to go to see this blog all the time.
Thanks for the good writeup. It actually used to be a entertainment account
it. Glance complex to far brought agreeable from you!
However, how could we keep in touch?
Very interesting details you have noted, thank you for
putting up.
Where other battery cases use a micro-USB connector and their own energy cables,
we designed the Battery Photo Case with a lighting connector, enabling you to use your customary Apple cables.
One which delivered on the promise of power without the extra bulk.
Helping folks around the world was one of the best option to make some further change, until really determined.
Because we like to supply a bit further control, you may flip charging settings on and
off inside the Moment App, one thing most different battery
instances don’t present. Case packs a 3500 mAh
battery and the iPhone 7 carries a 2500 mAH battery. To all the shoppers who requested for a skinny,
non-electronic Moment case — this one’s for you.
Every Moment product starts with the shopper. From amateurs to professionals, picture takers to filmers,
we studied their complete buyer journey nicely earlier than we
started designing any solutions. The case might be constructed with leather-based and it may be handcrafted as properly.
The prosecution might agree to cut back the quantity of expenses as effectively.
During a typical trial their can be opening statements by each the prosecution and the defence.
By opening up the optics with this lens, we are actually in a position to deliver edge to edge
readability on iPhone 7, Google Pixel, and the Galaxy S7.
My developer is trying to persuade me to move to .net from PHP.
I have always disliked the idea because of the
expenses. But he’s tryiong none the less. I’ve been using
WordPress on numerous websites for about a year and am nervous about switching to another platform.
I have heard great things about blogengine.net. Is there a way I can transfer all my wordpress posts
into it? Any kind of help would be really appreciated!
For the reason that the admin of this website is working,
no hesitatiion very quickly it will bee famous, due to its quality contents.
Wonderful website you have here but I was curious if you knew of any forums
that cover the same topics discussed in this article? I’d really love to be a part of group where I can get
responses from other knowledgeable people that share the same interest.
If you have any recommendations, please let me know. Bless you!
Hello, everything is going fine here and ofcourse every one is sharing information, that’s truly excellent, keep
up writing.
On line casino games have normally been favored sources of enjoyment, as very well as a way of winning cash for several people in many nations all over five continents
through generations. In the earlier, the club Craven’s has obtained legendary status
for its decadent performs. In present-day times, tourist magnets this kind of as Las
Vegas and Macau owe their popularity in part to their
glamorous, large-stakes casinos supplying actually
hundreds of gaming alternatives for avid gamers searching for classy entertainment, deep plays,
and a prosperity of winnings.
With the resurgence of the Online in the earlier 10 years and the increase of social
networking web pages in latest many years, casino gaming has also uncovered its way on-line.
Gaming on web sites is now using up huge bandwidths as a lot more and additional people get hooked on on-line blackjack, poker, roulette, slots
devices or any of the other casino online games readily available on the web.
On line gaming has observed a steep increase in acceptance due
to a lot of factors.
Foremost of this is economic. When the stereotype of gamers are those people higher-rolling, accommodate-clad millionaires with bottomless pockets, the
fact is that many gamers have only just plenty of to take pleasure in a couple good rounds of enjoy and a bit of enjoyment
on the aspect. In the confront of the financial downturn, quite a
few players who adore casino game titles have discovered by themselves strapped for income.
On-line on line casino online games present players the opportunity to get pleasure
from their preferred games with out acquiring to shell out added for journey
expenditures from their houses to casinos. In lots of cases, the on the net variation of on line casino games even eliminates solely the need
to have for players to shell out hard cash,
what with the increase of absolutely free activity downloads.
Accessibility is also an additional factor facilitating the increase of on the internet on line casino
gaming popularity. People today strapped for time-businessmen and specialists tied up to their work, mother and father who cannot leave their young children alone, students fully commited
to their scientific tests-can very easily connect to their favourite on the
internet gaming web-site, enjoy taking part in their activity for the period that they can spare, then easily swap back
again to their responsibilities when required.
Social networking, much too, has played such a big component in introducing
and encouraging new and previous gamers alike to
actively play online on line casino online games. Due to the fact the gamers now get pleasure from the
activity with other people, typically their close friends,
family members and acquaintances, the feeling of soulless participate in with only technologies as game lover or opponent
has been largely dispelled. The enjoying circles also easily widen for the
reason that persons in social networking web pages actively attain out to
their contacts and invite them for a spherical of poker or roulette.
With the rise of on-line gaming, some web pages has also devoted them selves
to winnowing out the greatest on the internet gaming internet sites from the hundreds that can be found in webscape.
These features assessments of every single online gaming casino,
together with reward and no cost gift gives, for reference
and satisfaction of consumers who want only the very best working
experience. Such web pages serves as gateway to a multitude of casino game titles.
The rise of reputation of on line on line casino
gaming does not appear to be to be slowing down. In simple fact,
the range of websites devoted to these, the avid players,
and number of performs per person are however meteorically capturing up.
I don’t even understand how I stopped up here, however I thought
this put up was good. I don’t know who you’re but certainly you
are going to a famous blogger when you are not already. Cheers!
Interessante Homepage. Das Design und die nuetzlichen Informationen gefallen mir besonders.
Thankѕ for mаking tһe honest attempt to write regarding tһis.
It may ƅe extremely helpful fߋr me and my friends.
With havin so much content do yyou ever run into any issues of plagorism or copyright infringement?
My site has a lot of exclusive content I’ve eiher created myself or outsourced but itt appears a loot of it is poping it up aall over the web
without my agreement. Do youu know any techbniques to help protect against content from being
stolen? I’d genuinely appreciate it.
I used to be able tto find good information from your articles.
You could certainly see your expertise in the article you write.
The world hopes for more passionate writers such as you who aren’t
afraid to say how they believe. At all times follow your heart.
Casino game titles have constantly been most loved sources of entertainment, as well as a way of successful funds for several people in several nations all in excess
of five continents during generations. In the past, the club Craven’s has achieved
famous position for its decadent performs. In modern day moments, tourist magnets
these as Las Vegas and Macau owe their attractiveness
in part to their glamorous, large-stakes casinos providing pretty much hundreds of gaming possibilities
for avid gamers hunting for tasteful leisure, deep plays, and a prosperity
of winnings.
With the resurgence of the Internet in the earlier
10 years and the increase of social networking websites in current a
long time, casino gaming has also observed its way
on the internet. Gaming on websites is now having up large bandwidths as a lot more and far more people get hooked on online blackjack, poker, roulette, slots equipment or any of
the other on line casino online games accessible online.
On the web gaming has witnessed a steep increase in popularity because of to lots of factors.
Foremost of this is economic. Even though the stereotype of players are those people
large-rolling, suit-clad millionaires with bottomless pockets, the reality is that several players have only just adequate
to get pleasure from a couple good rounds of enjoy and a little
bit of entertainment on the facet. In the encounter of the
economic downturn, numerous gamers who enjoy casino game titles have located them selves strapped for
income. Online casino video games give players the possibility to love their most loved games without
the need of obtaining to invest added for vacation charges from their properties to casinos.
In a lot of occasions, the on the internet model of on line
casino online games even removes totally the will need for players to
shell out funds, what with the rise of cost-free sport downloads.
Accessibility is also a further element facilitating the increase of on the internet casino gaming attractiveness.
People strapped for time-businessmen and professionals tied up to
their get the job done, moms and dads who can not depart their young children on your own, students committed to their experiments-can simply join to their beloved on line gaming web site, appreciate actively playing their game
for the interval that they can spare, then quickly
change again to their duties when essential.
Social networking, as well, has performed this kind of a massive portion in introducing and encouraging
new and previous players alike to actively participate in on line casino
games. Since the gamers now love the game with other folks,
generally their friends, family members and acquaintances, the sensation of
soulless engage in with only engineering as sport companion or opponent has been mostly dispelled.
The playing circles also simply widen because individuals in social networking websites actively attain out to their contacts and invite them for a round of poker or roulette.
With the rise of on the net gaming, some sites has also devoted themselves to
winnowing out the very best on line gaming web sites from the hundreds that can be observed in webscape.
These capabilities assessments of every single on-line gaming casino, together with reward and absolutely free reward presents, for reference and enjoyment of
people who want only the best practical experience.
These internet sites serves as gateway to a multitude of on line casino games.
The rise of recognition of on the net on line casino gaming does
not appear to be to be slowing down. In point, the amount of sites devoted to these kinds of, the avid players, and number of performs per person are nevertheless meteorically shooting up.
Үоu arе ɑ really powerful writer. Ӏ can easily ѕee tһis in your article.
You have ɑ ᴡay of writing powerful infߋrmation tһat sparks much
interеst.
Howdy I am so happy I find your site, I truly found you by mistake, while
I was looking on search engines for something else, Anyways I’m here now and could just like to say cheers for a
remarkable post and interesting site. Please do keep up the truly great work.
Outstanding post,I will spend more time exploring
this topic.
You’re so cool! I don’t suppose I’ve truly
readd anhthing like this before. So nice to discover someone with a few original thoughts on this topic.
Really.. thanks for starting this up. This site is one thing that iis needed on the internet, smeone with a
bit of originality!
With the in no way-ending improvements in our Real Estate Marketplaces genuine estate
gurus are setting up to spend focus to the audio of
new fee streams of cash flow. Some realtors have either shied away
or ran-absent from these conditions as “Cap Price,” &
“Hard cash-on-Dollars Returns.” Terms that only the ‘smart’ and ‘numbers-oriented folks use to determine
if a True Estate order is a “Very good Deal”, or not.
A majority of the realtor brethren attended authentic estate
faculty due to the fact they are enthusiastic and passionate
about the promise of advertising serious estate and earning a fantastic living.
That getting reported “Moments are a Modifying.” Even if
you are living in a Sizzling Marketplace exactly where residential authentic estate sells in 2-3 times there
is an outdated strategy to true estate that is increasing more rapidly by the day…..Residential Genuine Estate Buyers.
This deft group of real estate buyers is having true estate and
the real estate financial investment globe into a new era!
No extended accepting the crazy volatility of the Dow Jones and
NASDAQ people. Unwilling to settle for the investment decision methods of their fore-fathers these Traders throw caution to the wind for returns over
the regular five-six% in their Roth or IRA accounts. These Buyers are daring and oftentimes intense.
Present-day True Estate Traders are all about the quick repair-n-flip, superior appreciation, and rock good regular funds-flows.
Chopping their teeth on financial commitment in their
individual residence-cities is only the commencing as the
Really serious Traders transform to details outside the house their very own back-yards to other
regions that demonstrate greater promise and
greater returns. You may say nicely how does this more mature grownup perspective their investment decision opportunities?
For starters the age of these stealth hunters
ranges from 28 to sixty eight. From “Loaded Dad-Lousy Father” e
book collection to Trumps magical presence on “The Apprentice,”
the younger real estate entrepreneurs are creating their dreams transpire to the
tune of three-5 acquisitions a year! Obtained your focus now?
The usual Investor has great to good credit history scores.
Great cash reserves or concealed resources of partners with
cash, and a willingness to make the offer occur at almost any expense.
The best held solution of all is that these investing beasts vacation in packs.
Wherever you see one a different is quite near guiding. In other phrases they know
the men and women that you want to know to expand your trader database even larger.
If the actual estate expert does a excellent occupation the happy consumers are
probable to refer quite a few of their fellow-traders.
Not just trader clientele but their typical each individual-working day genuine estate
company. Encounter it, if you can reveal to your
consumers how adept you are with their premier
private buy of authentic estate, then wouldn’t you suppose
they will be in excess of their “trustworthy true estate advisors”
impression on buying a simple dwelling, condo or beach front home?
So what if you haven’t been focused in the true estate financial investment sector.
And you are contemplating this all sounds pretty fantastic, let us give it a test.
Very first issue to inquire you is who have your shoppers been doing the job with or checking out
their alternatives of true estate investing with around the
past three-four months. Statistically 6 out of ten purchasers have regarded investing in serious estate or have presently started doing so in advance of their
realtor even has a opportunity to blink an eye. Obtained your focus now?
How about the truth that in significantly less than one calendar year I increased my
annual commissions by 30% by just positioning myself inside my major knowledge-foundation of consumers.
All I did was enable them know that I was all set, prepared and capable to start off
assisting them with their “Expense Realty” wants. What I learned in the course of the 1st calendar year was that if I could generate an ecosystem for my customers to understand much
more about actual estate investing that they would thank me in a
wide range of techniques….Most importantly they would contact me prior to creating a contract and would
make absolutely sure that I was associated in just about every agreement that needed to make a true estate invest
in. In advance of very long 30% went up to forty five% and even further.
Even if you are not intrigued in expanding your consumer database, at least consider guarding the turf
you have for so long expended tireless amounts of time and financial resources to sustain their allegiance.
On the other hand if you are searching at your genuine estate profession and are thinking how to reposition by yourself for market progress unquestionably to go effectively into 2025, listed here are
a several identified points about how true estate investors can make improvements to your business enterprise.
1.Actual Estate Buyers are actually everywhere you go.
Efficiently tapping into your current databases could boost your yearly commissions by twenty-thirty%.
2.Genuine Estate Investors will be faithful to the experienced that can help
fill the hole of their investment training. Workshops,
mentoring groups, locating the “golden offers” in your sector will make a massive impression!
three.Investing in Actual Estate Buyers isn’t going to have to suggest that you reduce your
“common” household real estate agent situation. Staying a true estate financial investment professional means you are smarter
than the typical realtor in the market place.
four.Home finance loan experts are struggling to deliver authentic estate investors
with home bargains, so when you can put an investor into a good offer the referrals will start out to
movement even much more.
5.Real Estate Buyers are inclined to be much more conscientious about your own time absent.
Investors also like to shop Monday-Friday for their deals just before the “Weekend Warrior” investors get out into
the competitiveness. This interprets into much more usual hours and times of procedure for you and your company.
6.Actual Estate Traders obtain-offer cycles are shorter than primary residence
purchasers resulting in far more transactions in shorter time-frames.
With the hardly ever-ending adjustments in our Real Estate
Markets real estate experts are beginning to spend notice to the sound of new commission streams of profits.
Some realtors have either shied absent or ran-away from
these types of phrases as “Cap Rate,” & “Income-on-Hard cash Returns.” Terms that only
the ‘smart’ and ‘numbers-oriented folks use to decide if a Serious Estate order
is a “Fantastic Deal”, or not. A bulk of the realtor brethren attended real estate faculty because they
are excited and passionate about the guarantee of selling
authentic estate and producing a great dwelling. That becoming reported “Moments are a Changing.”
Even if you dwell in a Very hot Market where by residential authentic
estate sells in 2-three times there is an previous
solution to serious estate that is expanding quicker by the day…..Residential Actual Estate Buyers.
This deft group of genuine estate investors is having real estate and the real estate expenditure entire world into a new era!
No for a longer period accepting the nuts volatility of the Dow Jones and
NASDAQ family members. Unwilling to accept the expenditure practices of
their fore-fathers these Traders throw warning to the wind for returns earlier mentioned the traditional 5-6% in their Roth or
IRA accounts. These Traders are daring and in many cases aggressive.
Modern Serious Estate Buyers are all about the fast fix-n-flip, significant appreciation, and rock good every month income-flows.
Chopping their enamel on expense in their personal
property-towns is only the commencing as the Critical Buyers turn to details outside their individual back-yards to other
regions that exhibit bigger assure and bigger returns.
You may well say well how does this more mature adult look at their financial commitment prospects?
For starters the age of these stealth hunters ranges from 28 to 68.
From “Abundant Father-Lousy Father” e book series to Trumps magical existence
on “The Apprentice,” the young serious estate business
owners are producing their desires happen to the tune of three-five acquisitions a calendar year!
Received your focus now? The common Trader has good to great credit history scores.
Superb funds reserves or concealed means of companions with income, and a willingness to make the deal come about at almost any price
tag. The very best stored solution of all is that these investing beasts journey in packs.
The place you see a single yet another is quite near driving.
In other terms they know the people today that you need to know to improve your investor database
even larger sized. If the serious estate expert does a fantastic position the pleased shoppers are possible to refer a lot of of their fellow-buyers.
Not just trader shoppers but their standard each-working day actual estate small business.
Confront it, if you can demonstrate to your clients how adept
you are with their largest personal obtain of authentic
estate, then would not you suppose they will be more than their “trustworthy true estate advisors” view on obtaining
a simple home, condominium or beach dwelling?
So what if you haven’t been focused in the authentic estate financial investment sector.
And you are thinking this all sounds pretty very good, let us give it a try out.
Initially concern to check with yourself is who have your purchasers been operating with or exploring their
selections of real estate investing with around
the previous 3-4 months. Statistically 6 out of
10 consumers have regarded investing in real estate or have by now started carrying out so right before their
real estate agent even has a possibility
to blink an eye. Bought your interest now?
How about the reality that in significantly less
than a single year I increased my annual commissions by 30% by just positioning myself in my main data-foundation of clients.
All I did was let them know that I was completely ready, inclined and able to start out helping them
with their “Financial commitment Realty” needs.
What I learned in the course of the first yr was that if I could build
an surroundings for my consumers to understand additional about real
estate investing that they would thank me in a range of approaches….Most importantly they would contact me just before creating a contract and would make sure that I was concerned in every single agreement that preferred
to make a authentic estate invest in. In advance of extensive thirty% went
up to 45% and further. Even if you are not fascinated in growing your client
databases, at least contemplate shielding the turf
you have for so prolonged put in tireless amounts
of time and fiscal sources to maintain their allegiance.
On the other hand if you are seeking at your actual estate occupation and are asking
yourself how to reposition yourself for market development surely to go nicely into 2025, below are a several recognized details about
how genuine estate buyers can make improvements to your business enterprise.
one.Real Estate Investors are pretty much everywhere.
Effectively tapping into your recent database could
enhance your once-a-year commissions by twenty-thirty%.
two.Real Estate Investors will be faithful to the qualified that can help fill the gap of their investment schooling.
Workshops, mentoring teams, discovering the “golden specials” in your market
can make a huge influence!
3.Investing in Real Estate Traders isn’t going to have to signify that you reduce your “common” residential real estate agent situation. Being a serious estate financial commitment specialist
implies you are smarter than the average realtor in the sector.
four.Home loan gurus are having difficulties to present genuine estate traders with home discounts,
so when you can put an investor into a good deal the referrals will begin to circulation even a lot more.
five.Genuine Estate Investors have a tendency to be additional conscientious about your individual time absent.
Investors also like to shop Monday-Friday for their specials ahead of the “Weekend Warrior” traders get out into the levels of
competition. This interprets into far more usual several hours
and days of operation for you and your organization.
six.Real Estate Investors invest in-provide
cycles are shorter than key household purchasers ensuing in more
transactions in shorter time-frames.
Excellent items from you, man. I’ve be aware your stuff previous to and
you’re just extremely excellent. I really like
what you’ve acquired here, really like what you’re stating and the way during which you assert it.
You make it entertaining and you continue
to care for to keep it smart. I cant wait to learn much more from you.
This is really a tremendous website.
Buy it now.
Thank you for any other informative web site.
The place else may I get that kind of info written in such a perfect way?
I’ve a project that I’m just now working on, and I’ve been on the glance out for such information.
Nice response in return of this question with real arguments and explaining
all regarding that.
It’s a shame you don’t have a donate button! I’d certainly donate to this outstanding blog!
I guess for now i’ll settle for bookmarking and adding your
RSS feed to my Google account. I look forward to
fresh updates and will share this site with my Facebook group.
Talk soon!
It’s amazing to pay a visit this website and reading the views of all mates regarding this post, while I am also zealous of getting experience.
Hi, its pleasant article concerning media print, we all be familiar with media is a impressive source of facts.
May I just say what a comfort to find somebody that
actually knows what they’re discussing on the internet.
You certainly know how to bring an issue to light and make it important.
More and more people really need to look at this and understand this side
of your story. I can’t believe you’re not more popular since
you surely possess the gift.
Pretty! This was a really wonderful article. Thank you
for supplying this info.
Awesome issues here. I’m very glad to peer your post.
Thanks so much and I’m having a look forward to contact
you. Will you please drop me a e-mail?
I am regular reader, how are you everybody?
This post posted at this web page is genuinely nice.
Right here is the right webpage for everyone
who really wants to understand this topic. You
know a whole lot its almost hard to argue with you (not that I
really would want to…HaHa). You definitely put a
fresh spin on a subject that’s been written about for ages.
Wonderful stuff, just great!
If you are going for best contents like myself, just pay a visit this
web site daily as it presents quality contents, thanks
I think that what you published was very logical. However, think about
this, what if you were to write a killer headline?
I ain’t saying your content isn’t solid., but what if you added a headline that grabbed
a person’s attention? I mean Causes of variation in firearm homicide and suicide rates across states.
– Dr. Jon B. is kinda boring. You might look at Yahoo’s home page
and note how they create article titles to get people interested.
You might add a related video or a related pic or two to get
people interested about what you’ve got to say.
In my opinion, it would bring your posts a little bit
more interesting.
Hi, yes this article is actually good and I have learned lot
of things from it about blogging. thanks.
I do not know if it’s just me or if perhaps everyone else experiencing problems with your website.
It appears as though some of the written text on your content
are running off the screen. Can somebody else please provide feedback
and let me know if this is happening to them as well?
This may be a issue with my web browser because I’ve had this happen previously.
Thank you
Can I just say what a relief to discover somebody who truly knows what they’re talking about online.
You definitely understand how to bring an issue to light and make it important.
A lot more people really need to check this out and understand this side of the story.
I can’t believe you are not more popular given that you surely have the gift.
Hello friends, its enormous paragraph concerning cultureand fully explained, keep
it up all the time.
Thee broad spectrum of dances includes contemporary, classical, ballroom, street, jazz,
hip-hop, musocal theatre andd every one of their sub-genres.
From Barmans online, you should have the whole bar and catering
materials covered-along using your home bar ass well as your outdoor dining set up.
Hilary Duff aoso became a singer from being just a star of her own Disney Channel show, Lizzie
Maguire.
Very quickly this website will be famous amid all blogging visitors,
due to it’s pleasant articles
It is truly a great and useful piece of information. I’m glad that you just shared this useful information with us.
Please keep us informed like this. Thanks for sharing.
Can I simply just say what a relief to uncover an individual who genuinely
understands what they are talking about on the web.
You definitely know how to bring an issue to light and make it important.
More and more people ought to check this out and
understand this side of your story. I can’t believe you’re not more
popular since you surely possess the gift.
Very quickly this web page will be famous amid all blog viewers, due to it’s good
posts
Klasse gemachte Seite, das Layout gefaellt mir sehr gut!
War bestimmt ‘n haufen Aufwand.
whoah this blog is wonderful i really like studying your articles.
Stay up the good work! You realize, loots of persons are searching round for this info, you ccan help them greatly.
Simply wish to say your article is as surprising.
The clearness in your post is just spectacular and
i can assume you’re an expert on this subject. Fine with your
permission let me to grab your feed to keep up
to date with forthcoming post. Thanks a million and
please keep up the gratifying work.
First off I want to say great blog! I had a quick question that I’d like to ask if
you do not mind. I was interested to find out how you
center yourself and clear your head before writing.
I have had a difficult time clearing my thoughts in getting my thoughts out there.
I truly do take pleasure in writing however it just seems like the first 10 to 15
minutes are usually lost simply just trying to
figure out how to begin. Any suggestions or hints?
Many thanks!
This website definitely has all the information and facts I wanted concerning this subject and didn’t know who to ask.
Quality articles is the crucial to be a focus for
the users to pay a visit the site, that’s what this web site is
providing.
Useful info. Lucky me I found your site by chance, and I’m surprised why this accident
didn’t happened in advance! I bookmarked it.
Wow, awesome weblog structure! How long have you ever been running a blog for?
you make running a blog glance easy. The entire look of your website is magnificent, as smartly as the content!
Appreciating the time and energy you put into your blog and
detailed information you present. It’s awesome to come across a blog every once in a while that isn’t the same out of date rehashed information. Fantastic read!
I’ve saved your site and I’m including your RSS feeds to my Google account.
Excellent goods from you, man. I’ve understand your stuff previous
to and you’re just too great. I really like what you’ve acquired
here, certainly like what you’re saying and the way in which you say it.
You make it entertaining and you still care for to keep
it sensible. I can’t wait to read much more from you.
This is really a terrific web site.
I got this website from my friend who shared with me concerning this web page and now this time I
am visiting this web site and reading very informative content here.
Hi to all, it’s in fact a nice for me to go to see
this web site, it consists of important Information.
Nice respond in return of this question with firm arguments and telling all about that.
Hello everyone, it’s my first go to see at this
web site, and article is really fruitful in support of me,
keep up posting these content.
Have you ever thought about writing an ebook or guest authoring
on other blogs? I have a blog centered on the same subjects you discuss and would really like to have you share some stories/information. I know my viewers
would enjoy your work. If you are even remotely interested, feel free to send me an e mail.
What’s Going down i am new to this, I stumbled upon this I have
discovered It positively useful and it has helped me out loads.
I hope to give a contribution & assist other customers like its aided me.
Great job.
Awesome blog! Do you have any tips for aspiring writers?
I’m hoping to start my own blog soon but I’m a little lost on everything.
Would you suggest starting with a free platform
like WordPress or go for a paid option? There are so many choices
out there that I’m totally overwhelmed .. Any ideas?
Cheers!
Now I am going to do my breakfast, when having my breakfast coming over again to read more news.
What a information of un-ambiguity and preserveness of valuable knowledge
concerning unexpected feelings.
It’s actually very complicated in this busy life to listen news on TV, so I simply use
the web for that reason, and get the most recent news.
Amazing! Its actually amazing post, I have got much clear idea on the topic of from this post.
Good replies in return of this question with
real arguments and explaining the whole thing concerning
that.
Informative article, totally what I needed.
Hello! This is my first visit to your blog! We are a team of volunteers and starting a new initiative in a community
in the same niche. Your blog provided us valuable information to work on. You have done a wonderful
job!
I’m gone to convey my little brother, that he should also visit this web site on regular basis to obtain updated from newest news update.
This is my first time pay a visit at here and i am really impressed to read everthing at one place.
Can you tell us more about this? I’d love to find out more details.
hi!,I love your writing so much! proportion we keep in touch extra about your post
on AOL? I need a specialist on this house to unravel my problem.
May be that is you! Looking forward to peer you.
It’s difficult to find educated people for this topic, but you sound like you know what
you’re talking about! Thanks
Right here is the right web site for anyone who hopes to find out about
this topic. You realize so much its almost hard to argue with you (not that I actually
will need to…HaHa). You definitely put a fresh spin on a subject that’s been written about for
decades. Excellent stuff, just excellent!
Great post. I was checking continuously this blog and I am inspired!
Extremely helpful information specifically the remaining
phase 🙂 I handle such info a lot. I was seeking this certain information for a long time.
Thanks and best of luck.
Thanks for sharing your thoughts about 하이 로우.
Regards
Glaad to bee one of sseveral visitors on this awingg web site :D.
I’ve been absent for a while, but now I remember why I used to love this website. Thanks, I will try and check back more often. How frequently you update your site?
fantastic issues altogether, you simply received a logo new reader.
What could you suggest in regards to your post
that you just made a few days in the past? Any positive?
Having read this I thought it was very enlightening.
I appreciate you spending some time and effort to put this information together.
I once again find myself personally spending a lot of time both reading and posting comments.
But so what, it was still worth it!
Hmm it seems ike your site ate my first comment (it was extremely long) so
I guess I’ll just sum it up whwt I had written and say, I’m thoroughly enjoying
your blog. I too am an aspiring blog writer bbut I’m still new to everything.
Do you have any tjps for beginner blog writers? I’d genuinely appreciate it.
Useful info. Fortunate me I discovered your website unintentionally, and I’m stunned
why this coincidence did not happened in advance!
I bookmarked it.
buy hacklink
I’m really loving the theme/design of your website. Do you ever run into any internet browser compatibility issues?
A number of my blog readers have complained about my website not operating correctly in Explorer but looks great in Opera.
Do you have any solutions to help fix this issue?
Hmm it looks like your website ate my first comment (it was super long) so I guess I’ll just sum it up what I had written and say, I’m thoroughly enjoying your
blog. I as well am an aspiring blog blogger but I’m still
new to everything. Do you have any tips for newbie blog writers?
I’d genuinely appreciate it.
thank you admin kardeş.
Le whisky sent la punaise ecrasee. Mais le contraire n’est pas vrai. http://www.sansordonnanceviagra.fr
thank you
Admin elinize sağlık thanx you.
Admin elinize sağlık thanx you. https://rakipsizsohbet.com/mobil/
Pretty! This has been a really wonderful post.
Thanks for providing this information.
good sohbet thanks
Hello very nice website!! Guy .. Beautiful .. Wonderful ..
I’ll bookmark your website and take the feeds also…I am glad to seek out numerous helpful info right
here within the submit, we’d like work out extra strategies
on this regard, thanks for sharing.
Oh my goodness! Amazing article dude! Thank you, However I am experiencing
troubles with your RSS. I don’t know why I am unable to join it.
Is there anybody else having similar RSS issues? Anyone who knows the answer can you kindly respond?
Thanks!!
I am in fact thankful to the holder of this web site who has shared this great
post at here.
Excellent article! We will be linking to this great article on our site.
Keep up the good writing.
Thanks for sharing your thoughts about here. Regards
Awesome things here. I am very glad to see your article.
Thank you so much and I’m taking a look forward to touch you.
Will you kindly drop me a e-mail?
This is really attention-grabbing, You are a very professional blogger.
I’ve joined your rss feed and sit up for looking for more of your excellent post.
Also, I’ve shared your website in my social networks
This is a really good tip especially to those fresh to the blogosphere.
Brief but very precise information… Thank you for sharing this
one. A must read article!
Right here is the perfect site for anybody who hopes to find out about this topic.
You understand so much its almost hard to argue with you (not that I actually would
want to…HaHa). You definitely put a new spin on a topic that’s been discussed for ages.
Wonderful stuff, just excellent!
การเล่นบาคาร่าออนไลน์นั้น พวกเราสามารถเลือกใช้สูตรนี้ ได้มากมาย สูตรแทงเงินต้นไปเรื่อยๆเป็นสูตรที่คนใช้กันมากมายก่ายกอง วิธีการใช้สูตรนี้คือให้เราจ่ายเงินก้อนเล็กๆสำหรับการเดิมพันคราวแรก แล้วเพิ่มเป็นสองเท่าครั้งใดก็ตามเราลงทุนซึ่งโน่นจะช่วยให้เราได้รับกำไรมากขึ้น
It is not my first time to go to see this web page, i am browsing this web page
dailly and take nice information from here every day.
thanks for share.
a great blog thank u
What’s Going down i’m new to this, I stumbled upon this I’ve discovered It
positively helpful and it has helped me out loads.
I am hoping to give a contribution & help other users like its aided me.
Good job.
Very rapidly this web site will be famous amid all blog people, due to
it’s nice articles
thank you admin bekleriz.
This paragraph on the topic of SEO provides clear picture in favor of new SEO users that how to do Search engine optimization, so keep it up. Good job https://cloud-mining.mobi
Hurrah, that’s what I was searching for, what a material!
present here at this web site, thanks admin of this site.
thank you admin bekleriz.
Thanks for finally writing about >Causes of variation in firearm homicide and suicide rates across states.
– Dr. Jon B. <Loved it!
I am not sure the place you’re getting your info,
however great topic. I needs to spend a while
learning more or working out more. Thank you for wonderful information I used to be searching for this information for my mission.
Hey there great website! Does running a blog such as this require a great deal of work?
I have absolutely no expertise in coding but I had been hoping to start my own blog soon. Anyway, if
you have any suggestions or techniques for new blog owners please
share. I know this is off subject however I simply needed to ask.
Cheers!
If you want to get a good deal from this
paragraph then you have to apply such methods to your won blog.
Thanks for finally talking about > Causes of variation in firearm homicide and suicide
rates across states. – Dr. Jon B. < Loved it!
I visit everyday some web pages and blogs to read articles
or reviews, but this blog gives quality based posts.
Fastidious replies in return of this difficulty with solid arguments and explaining the whole thing concerning that.
Remarkable! Its actually awesome article, I have got much clear idea about from this piece of writing.|
You need to be a part of a contest for one of the greatest blogs online.
I’m going to highly recommend this website!
What’s up everyone, it’s my first pay a visit at this site,
and article is genuinely fruitful in favor of me, keep up
posting such content.
Rattling clean site, appreciate it for this post.
Welcome everyone ! I’m Kyran Mckinney.
Even though I jokingly credit my grandmother for my writing talent, I know that it is a talent I have fostered from childhood. Though my grandmother is a writer, I also started out young.
I’ve always had a way with words, according to my favorite professor . I was always so excited in history when we had to do a research writing assignment.
Now, I help current pupils achieve the grades that have always come easily to me. It is my way of giving back to students because I understand the troubles they must overcome to graduate.
Kyran Mckinney – Academic Writing Professional – http://www.aa-mediastudies.net Band
Hello, all is going well here and ofcourse every one is sharing data, that’s in fact fine, keep up writing.|
I?m impressed, I must say. Rarely do I encounter a blog that?s both equally educative and amusing, and let me tell you, you have hit
the nail on the head. The problem is something that too few people are speaking intelligently about.
Now i’m very happy I found this in my hunt for something concerning this.
Can I simply just say what a comfort to discover a person that truly understands what they are discussing on the net. You actually realize how to bring a problem to light and make it important. More and more people really need to look at this and understand this side of the story. It’s surprising you’re not more popular because you certainly have the gift.
Unquestionably believe that which you stated. Your favorite reason seemed to be on the web
the easiest thing to be aware of. I say to you, I definitely get irked while people consider worries that they plainly do not know
about. You managed to hit the nail upon the top and also defined out the
whole thing without having side effect , people can take a signal.
Will likely be back to get more. Thanks
I’m amazed, I have to admit. Rarely do I encounter a blog that’s both equally educative and engaging, and let me tell you, you’ve hit the nail on the head. The issue is something which too few men and women are speaking intelligently about. I’m very happy I came across this during my search for something concerning this.
En effet, si cette fonctionnalité est positionnée sur « oui »,
alors seuls les modules présents par défaut dans votre boutique fonctionneront.
Cependant, j’ai rencontré beaucoup de commerçants qui s’étaient fait avoir car, juste en dessous du réglage «
Activer la boutique », il y a un champ nommé « IP de maintenance ».
Cependant, Shopify a également des directives strictes sur ce que vous ne pouvez pas vendre.
Cependant, WooCommerce et PrestaShop proposent tous les deux un niveau de sécurité satisfaisant.
WooCommerce est basé sur WordPress, une solution de blogue très facile d’utilisation, et est recommandable si vous avez peu de produits, peu de commandes, et peu de roulement de produits.
Si vous avez un peu de temps, mettez vos produits sur Amazon et profitez-en pour ouvrir votre boutique Amazon sous un autre nom afin de vendre
à un prix inférieur sans nuire à votre marque principale.
Dans un second temps, l’administrateur Shopify vous permet de suivre en temps réel le parcours
achat du client ajoutant un produit à son panier moyen ou effectuant un achat.
it’s way too transparent though. They should change the door.
Fantastic blog you have here but I was curious about if you knew of any message boards that cover the
same topics discussed in this article? I’d really love to be a
part of online community where I can get suggestions from
other experienced individuals that share the
same interest. If you have any recommendations, please let me
know. Thanks!
I really like reading your articles, your articles are very helpful for me and among young people
tesekkürler admin çok isime yarayacak bir bilgi.
Very soon this web page will be famous among all blog viewers, due
to it’s good posts
Celtabet güncel giriş adresi ile Celtabet üyelik ve kayıt işlemlerinizi yapabilirsiniz. Celtabet yeni giriş adresini takip edin!
Good post. I learn something new and challenging on sites I stumbleupon on a daily basis. It’s always useful to read articles from other authors and use a little something from other sites.
current articles. A personal blog is articles that can connect with people on a personal level by appealing to interests and emotions. It is also possible to benefit from visual materials in these articles. In this way, a bond can be established between the blog owner and people.
Very good post! We will be linking to this particularly great post on our site. Keep up the great writing.
Great post! We are linking to this great content on our website. Keep up the good writing.
Kendine uygun kız arkadaş edinmek istanbul.net sayesinde artık hem kolay hem … Kız arkadaş veya erkek arkadaş bulmak için ücretsiz arkadaşlık siteleri …
Tüm ambalaj ürünleriniz fibertedarik.com adresinde. Kraft çanta, karton bardak, plastik bardak, çorba kasesi, patates kutusu, burger kutusu ve daha bir çok ürün ile hizmetinizdeyiz.
That is really an great web
Full Apk İndir, Son Sürüm Apk